With the rise of social media and online communication, the threat of grooming has become a serious concern. As parents, understanding the signs of grooming and how to protect your kids is vital. This blog post delves into the 6 stages of grooming adults, offers practical advice for both parents and children and highlights tools like FamiGuard Pro to help keep your family safe.
Adult grooming is a manipulative process used by predators to exploit and abuse individuals. It involves building a relationship of trust and emotional connection to control and influence the victim. Recognizing the stages of grooming can help you intervene early and protect your loved ones.

Table of Contents
Part 1: The 6 Stages of Grooming Adults
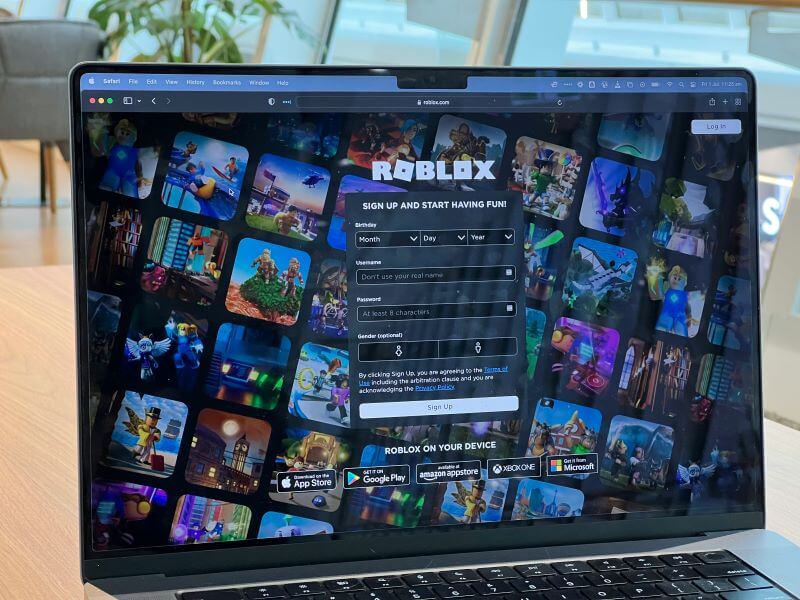
Let's examine the 6 grooming stages predators use to manipulate their victims. Understanding these stages can help you recognize the warning signs early and take action to protect your loved ones. Each stage builds on the previous one, gradually increasing the predator's control over the victim. Here are the detailed stages and what to look out for.
Source: The Psychology of Adult Sexual Grooming: Sinnamon’s Seven-Stage Model of Adult Sexual Grooming. Grant Sinnamon
Stage 1: Targeting the Victim
Predators often select their victims based on perceived vulnerability, such as loneliness or emotional distress. They are skilled at identifying those who seem isolated, unhappy, or need attention and support. By targeting someone who is already feeling vulnerable, the predator can more easily manipulate and control them. This stage sets the foundation for the entire grooming process, as it helps the predator identify someone they can exploit.
Behavior Examples:
- Predators might browse social media profiles to identify potential victims.
- They might join online groups or forums where vulnerable individuals are likely present.
Conversation Examples:
- "You seem like you really understand me."
- "I can tell you're different from others; we have a special connection."
Stage 2: Gaining Trust and Information
Once the predator has identified their target, the next step is to gain their trust. This stage involves creating a sense of friendship and emotional connection. Predators often share personal stories to form a bond, making the victim feel unique and understood. This tactic helps build trust and encourages the victim to open up about their own life. By establishing a seemingly genuine friendship, predators lower the victim's guard, making it easier to exploit them later.
Behavior Examples:
- Sharing personal stories to create a bond.
- Asking personal questions to gather information about the victim's life.
Conversation Examples:
- "Tell me about your family and friends."
- "I can tell you anything; you're a good listener."
Stage 3: Filling a Need
At this point, predators begin to exploit the victim's needs. They offer to fill emotional voids or provide support, making the victim feel valued and special. This might involve offering compliments and flattery to boost the victim's self-esteem or providing gifts and favors to create a sense of indebtedness. By filling a need, the predator deepens the emotional connection and dependency, making it more difficult for the victim to see through the manipulation and seek help from others.
Behavior Examples:
- Offering compliments and flattery to boost the victim's self-esteem.
- Providing gifts or favors to create a sense of indebtedness.
Conversation Examples:
- "You deserve to be treated so much better."
- "I'll always be here for you when you need me."
Stage 4: Isolation
As the relationship progresses, predators aim to isolate the victim from their support network. Isolation is a key tactic predators use to exert more control over their victims. They encourage the victim to distance themselves from friends and family, often by creating conflicts or planting seeds of doubt about the victim's support network. By isolating the victim, the predator reduces the likelihood of the victim seeking help or support from others. This makes the victim more reliant on the predator, further deepening the manipulative bond and increasing the predator's control over the victim.
Behavior Examples:
- Encouraging the victim to distance themselves from friends and family.
- Creating conflicts between the victim and their support network.
Conversation Examples:
- "Your friends don't really care about you like I do."
- "Your family doesn't understand you; they're holding you back."
Stage 5: Sexualizing the Relationship
As the predator's control over the victim deepens, they begin to introduce sexual content and behavior into the relationship. This stage often starts subtly, with the predator sending explicit messages or images or engaging in inappropriate conversations or actions. The goal is to desensitize the victim to sexual content and make it seem like a natural progression of their relationship. By sexualizing the relationship, the predator shifts the dynamic, making it harder for the victim to recognize the abuse and increasing the predator's control.
Behavior Examples:
- Sending explicit messages or images.
- Engaging in inappropriate conversations or actions.
Conversation Examples:
- "You're so attractive, I can't stop thinking about you."
- "This is our little secret; no one else would understand."
Stage 6: Maintaining Control
Once the predator has established control, they use various tactics to maintain their hold over the victim. This often involves manipulation, threats, and guilt to keep the victim compliant. The predator might threaten to reveal private information or use emotional blackmail to make the victim feel trapped. They may also make the victim feel indebted or guilty, reinforcing their control. By maintaining control, the predator ensures they can continue to exploit the victim without interference. This stage can last for an extended period, with the predator constantly reinforcing their control and manipulation.
Behavior Examples:
- Threatening to reveal private information.
- Using emotional blackmail to keep the victim compliant.
Conversation Examples:
- "If you tell anyone, I'll ruin your life."
- "You owe me for everything I've done for you."
Part 2: What to Do If Suspecting Grooming
If your child or someone you know, even yourself, suspects is experiencing grooming, you need to take action immediately. Knowing what steps to take can make a significant difference in preventing further manipulation and abuse. Here's what parents and children should do if they encounter grooming adults.
For Parents:
- Recognize the Signs: Be aware of changes in your child's behavior or emotional state.
- Open Communication: Encourage your child to talk openly about their online interactions.
- Educate: Teach your children about the dangers of grooming and how to recognize inappropriate behavior.
- Report the Incident: Report the behavior to the platform where the grooming occurred (social media, messaging apps, etc.). Contact local authorities and provide them with all the information you have.
- Seek Support: Talk to a trusted adult, friend, or family member about what is happening. Consider reaching out to professional counselors or hotlines that specialize in dealing with grooming and online exploitation.
- Preserve Evidence: Keep records of all communications (messages, emails, screenshots) as evidence.
For Children:
- Trust Your Instincts: If something feels wrong, it probably is.
- Seek Help: Talk to a trusted adult if you feel uncomfortable or threatened.
- Do Not Share Personal Information: Be cautious about sharing personal details online.
- Report: Use the reporting features on social media platforms and apps to report suspicious behavior.
Part 3: How to Prevent Online Grooming
Preventing grooming is all about being proactive and vigilant. By educating and protecting your children, you can reduce the risk of them becoming victims of grooming. Here are some effective methods to prevent online grooming.
Use Parental Control Tools - FamiGuard Pro
It is hard and impossible for parents to pay attention to kids' lives all the time, especially for the digital life. That's why sometimes having a parental control tool will be a helpful choice.
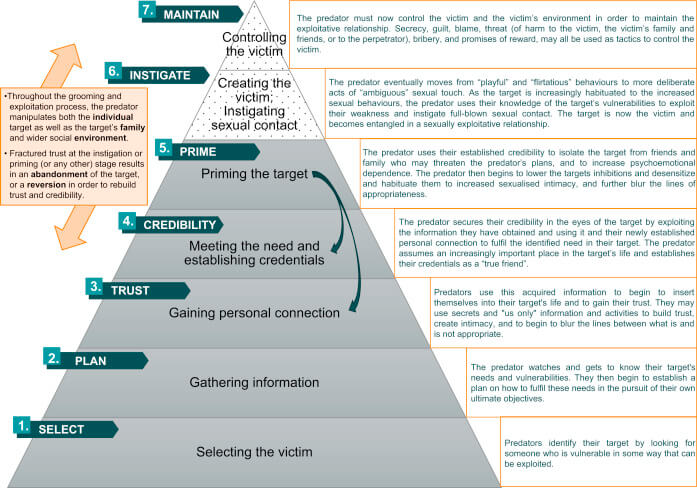
Using FamiGuard Pro is an effective strategy to prevent online grooming and keep your child safe. This comprehensive parental control tool allows you to monitor your child's online activity closely, including tracking text messages, social media interactions, and browser history. With real-time alerts, FamiGuard Pro notifies you instantly if suspicious keywords or phrases are detected, allowing you to intervene promptly.
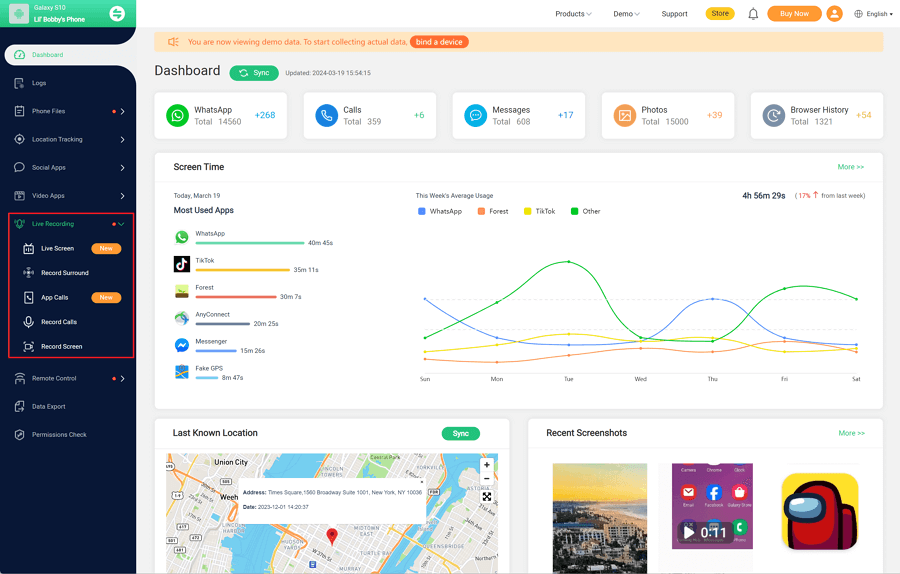
How to Set up Parental Control Tool FamiGuard Pro?
Step 1. Create/Sign in your account and pick the suitable subscription plan to unlock all FamiGuard Pro features.
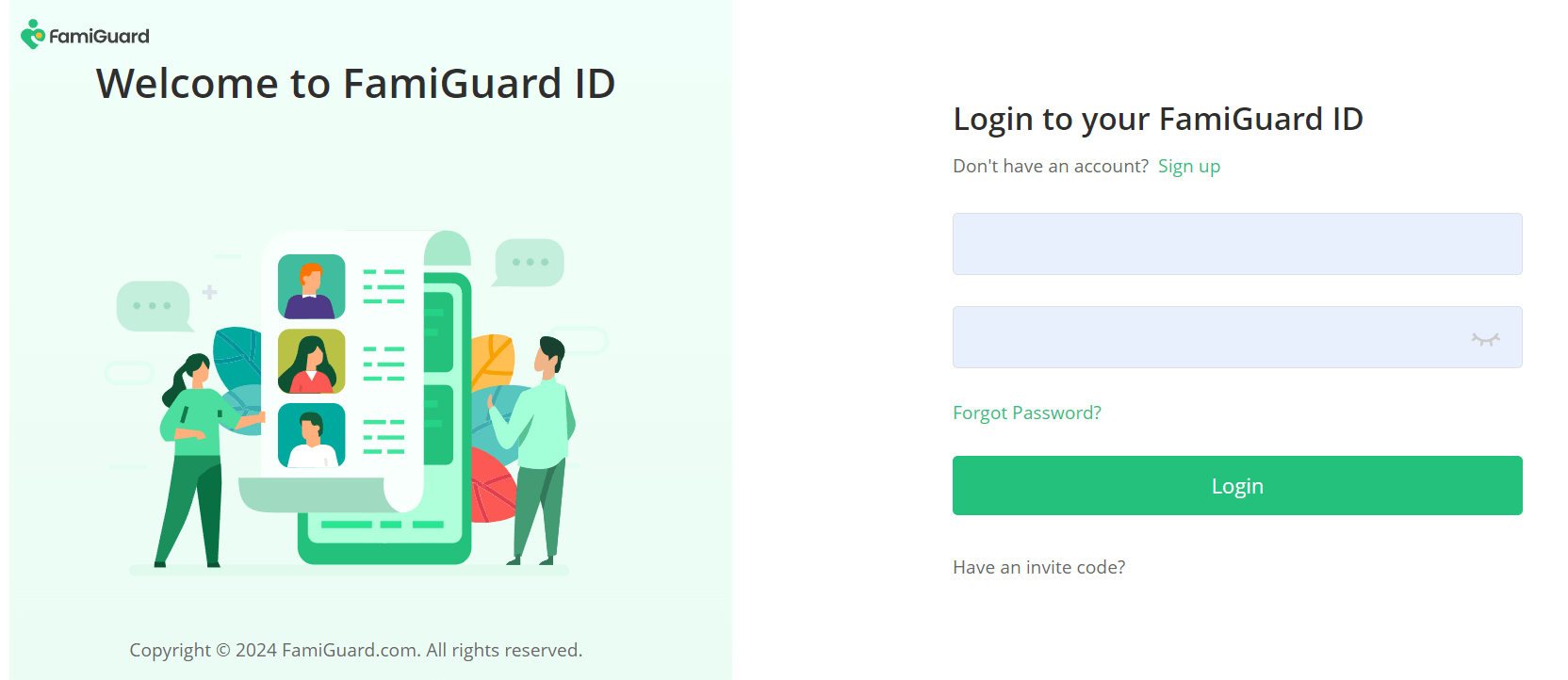
Step 2. After purchasing, you will be navigated to Member Center. Click Start Monitoring button and you will go to the dashboard, choose the device you want to bind and follow the Set up guide to finish installation and configuration.
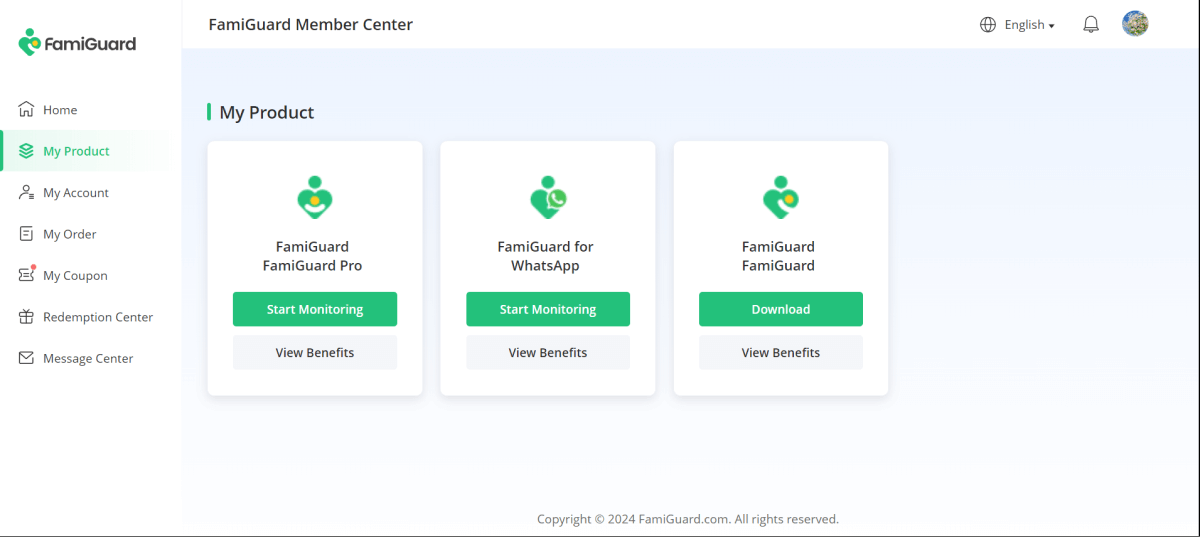
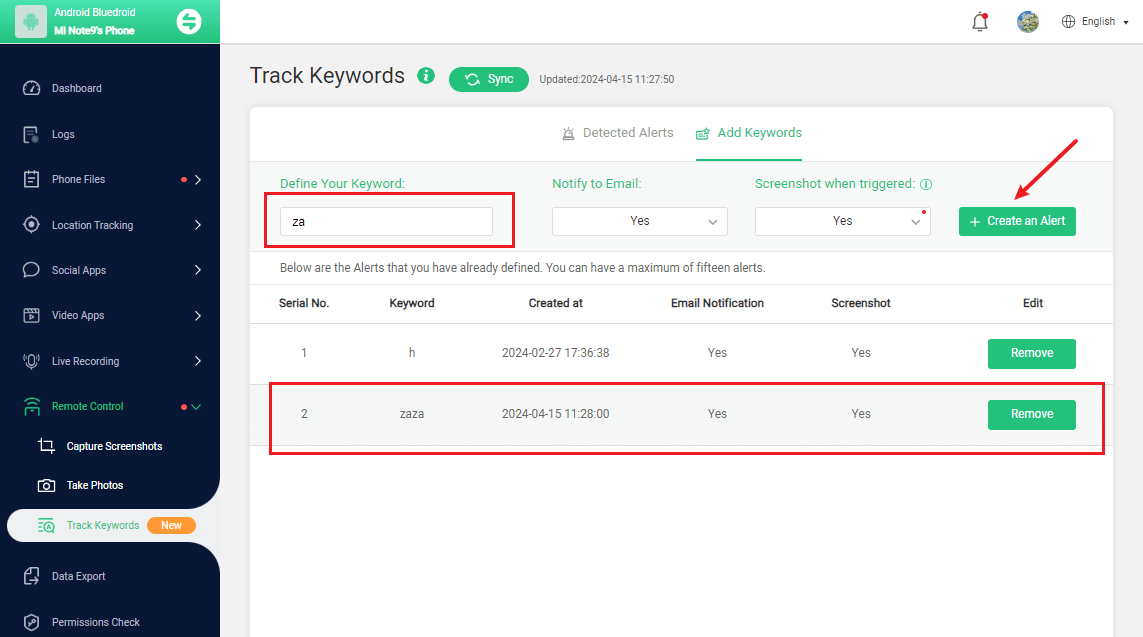
Step 3. If you verify your setup successfully, you can begin your monitor now. You can monitor social apps from Social Apps to find if there is something inappropriate conversations. What's more, it is useful to set keyword alert from Remote Control > Track Keywords, you can receive real-time notification with this.
Educate About Red Flags:
Teaching children about online grooming is essential. Explain the warning signs, such as strangers asking for personal information, sending inappropriate messages, or trying to isolate them from friends and family. Encourage open communication, letting kids know they can always come to you if they feel uncomfortable or suspicious about any online interactions. Role-playing scenarios can also help children recognize and respond to potential grooming tactics.
Use Technology Wisely:
Leverage parental controls and monitoring tools to keep an eye on your child's online activities. Set up privacy settings on social media accounts and restrict contact with unknown individuals. Encourage the use of safe, age-appropriate platforms and teach children about the importance of not sharing personal information online. Regularly review their friend lists and online interactions to ensure they're engaging with known and trusted individuals.
Stay Informed:
Stay updated on the latest trends in online behavior and potential threats. Join online safety forums, attend workshops, and follow reputable sources that provide information on online grooming and digital safety. Regularly discuss these topics with your child, ensuring they are aware of new risks and how to protect themselves. Being proactive and informed allows you to better safeguard your child’s online experiences.
FAQs
Q1: How can I recognize if my child is being groomed?
Look for signs such as secrecy, withdrawal from family and friends, or sudden changes in behavior.
Q2: What should I do if I suspect my child is being groomed?
Approach the situation calmly, talk to your child, and consider involving law enforcement or child protection services.
Q3: How effective are parental control tools like FamiGuard Pro?
They are highly effective in monitoring online activities and alerting you to potential dangers. Still, they should be used alongside open communication and education.
Conclusion
Grooming is a serious threat that requires vigilance and proactive measures. By understanding the stages of grooming and using tools like FamiGuard Pro, you can help safeguard your children from online predators. Stay informed, stay involved, and, most importantly, keep the lines of communication open with your kids. Your vigilance can make all the difference in protecting your family.

By Tata Davis
professional in software and app technology, skilled in blogging on internet
Thank you for your feedback!