FamiGuard Support: Monitor Devices with Others' Permission.
As cyber threats grow more sophisticated, organizations face increasing pressure to protect their sensitive data and systems from potential breaches. Cybersecurity monitoring has become a critical component of safeguarding digital assets. This comprehensive guide dives into computer security monitoring, exploring its significance in various domains, including cloud computing and 24/7 cyber security monitoring services.
The article aims to explain why security monitoring is important and the critical features of cyber security monitoring tools. It will examine essential techniques for effective monitoring and discuss the concept of continuous monitoring in cyber security. By the end, readers will have a deeper understanding of cyber security monitoring and its role in maintaining a strong security posture in our interconnected world.
Table of Contents
Part 1: What is Cyber Security Monitoring?
Part 2: Why Security Monitoring is Important
Part 3: Key Features of Cyber Security Monitoring Tools
Part 4: Types of Cyber Security Monitoring Services
Part 5: What is Continuous Monitoring in Cyber Security?
Part 6: Popular Cyber Security Monitoring Tools
Part 1: What is Cyber Security Monitoring?
Cyber security monitoring is continuously observing and analyzing an organization's IT infrastructure to detect and respond to potential security threats. This process involves rigorous surveillance of network traffic, endpoint behavior, servers, and logs to identify suspicious activities that could compromise data assets' integrity, confidentiality, and availability. By implementing cyber security monitoring, organizations can strengthen their cybersecurity posture and proactively address vulnerabilities before they escalate into full-fledged security incidents.
Key Components
Cyber security monitoring encompasses several vital components that work together to create a comprehensive security strategy:
- Network Security Monitoring: This detects performance issues or vulnerabilities that could indicate an attack. Standard tools include Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Behavioral Analytics (BA) systems.
- Endpoint Monitoring: This keeps track of devices like laptops, smartphones, and IoT devices connected to a network. Tools such as Endpoint Detection and Response (EDR) and Endpoint Protection Platforms (EPP) are commonly used.
- Log Management: This analyzes system, application, and security logs to provide valuable data and alert IT teams to potential security threats.
Real-time vs. Near-within a period of time Monitoring
Cyber security monitoring can be categorized into within a period of time and near-within a period of time approaches. Real-time tracking provides immediate threat detection, allowing organizations to respond instantly to potential security incidents. On the other hand, near-within a period of time monitoring operates with a slight delay, typically running at intervals of one to five minutes. While within a period of time monitoring offers the fastest response times, near-within a period of time monitoring can provide timely threat detection while balancing system resources and performance.
Part 2: Why Security Monitoring is Important
With the ever-increasing number of cyber threats, security monitoring has become essential to protecting sensitive information. The number of cyberattacks is rising yearly, targeting both large corporations and small businesses. Cybersecurity breaches can result in data theft, system damage, and financial loss, making it essential for organizations to take proactive measures.
Proactive security monitoring allows companies to detect and respond to threats before they escalate. Continuous monitoring ensures that any unusual activities or vulnerabilities are identified in within a period of time, reducing the risk of breaches. This proactive approach is far more effective than reacting to an attack after the damage has already been done.
Investing in security monitoring is an essential step in safeguarding business operations and ensuring compliance with data protection regulations. Companies can protect their assets, reputation, and customer trust by avoiding potential threats.
Part 3: Key Features of Cyber Security Monitoring Tools
Cybersecurity monitoring tools are essential for organizations to safeguard against evolving threats and vulnerabilities. Here are the key features these tools offer:
Real-time alerts and notifications
These features enable organizations to adopt a proactive stance against cyber threats by instantly notifying security teams of suspicious activities. By receiving immediate alerts about potential threats, security personnel can initiate timely investigations and implement preventive measures to mitigate risks.
Real-time alerting mechanisms help detect unusual activities that deviate from established behavior patterns, such as unauthorized access attempts, sudden data downloads, or access to sensitive information outside regular working hours. This immediate response capability minimizes the impact of security incidents and allows swift action against progress breaches.
Threat detection and analysis
Practical cyber security monitoring tools incorporate advanced threat detection and analysis capabilities. These features enable organizations to identify and assess vulnerabilities, detect anomalies, and respond to threats more accurately and quickly. By leveraging sophisticated algorithms and machine learning techniques, these tools can spot trends, patterns, and correlations that human analysts might miss, especially when dealing with vast volumes of security-related information.
Threat detection and analysis features typically include:
- Vulnerability scanning across networks, systems, applications, and assets
- Identification of misconfigurations, software flaws, and insecure settings
- Continuous monitoring and automated scans to assess risks and changes in security posture
- Integration with threat intelligence feeds to identify new and emerging cyber threats.
Reporting and auditing capabilities
Comprehensive reporting and auditing capabilities are essential features of cyber security monitoring tools. These functions provide organizations with valuable insights into their security posture, compliance status, and overall risk landscape. Detailed reports help security teams and stakeholders understand their security measures' effectiveness and identify improvement areas.
Key reporting and auditing features include:
- Generation of compliance audit reports for various standards and regulations (e.g., PCI DSS, HIPAA, GDPR, NIST)
- Customizable reporting templates for different organizational roles
- Vulnerability severity ranking and remediation guidance
- Historical data analysis for trend identification and security posture assessment
User activity monitoring and incident response
User activity monitoring (UAM) and incident response capabilities are critical components of cyber security monitoring tools. These features help organizations detect and respond to potential insider threats, compromised accounts, or unauthorized access attempts. By monitoring user behavior across the IT environment, security teams can identify suspicious patterns and take appropriate action to mitigate risks.
Key aspects of user activity monitoring and incident response include:
- Monitoring of user actions, including application usage, system commands, and data access
- Behavioral analytics to detect anomalies in user activity
- Integration with incident response workflows for rapid threat containment
- Forensic evidence collection for investigation and potential legal proceedings
Part 4: Types of Cyber Security Monitoring Services
When it comes to cyber security monitoring, organizations have several service options to choose from, depending on their specific needs and resources:
In-house Monitoring vs. Outsourced Services: In-house monitoring involves using internal teams to manage and monitor cybersecurity threats. This option gives organizations complete control but requires significant investment in tools, staff, and training. On the other hand, outsourced services involve hiring external experts to handle cybersecurity monitoring. Outsourcing is often more cost-effective and provides access to specialized knowledge without the need for continuous internal resource management.
24/7 Cyber Security Monitoring Services: Cyber threats can occur anytime, making round-the-clock monitoring essential. 24/7 monitoring services ensure that potential risks are detected and mitigated immediately, providing continuous protection. Automated systems and skilled security teams often support these services that offer immediate response capabilities, minimizing downtime and damage.
Managed Security Service Providers (MSSPs): MSSPs offer comprehensive security monitoring and management services, handling everything from threat detection to incident response. Organizations benefit from the expertise of MSSPs without needing to build an in-house security team. MSSPs also offer scalability, allowing businesses to adjust their security coverage based on their size and evolving needs. They are cost-effective for many organizations that need more dedicated IT security resources.
Each of these cyber security monitoring services offers unique advantages, and choosing the right one depends on the organization's goals, budget, and infrastructure.
Part 5: What is Continuous Monitoring in Cyber Security?
Continuous monitoring in cyber security is a proactive approach that involves the ongoing surveillance and analysis of an organization's IT infrastructure to detect and respond to potential security threats . Unlike traditional periodic monitoring, which collects data at set intervals, continuous monitoring analyzes data as collected, enabling immediate threat detection and response.
Continuous monitoring helps maintain protection by providing constant information about system health, performance, and security status.
A continuous monitoring system typically consists of several key features:
- Automated data collection: Various devices and agent plugins collect data from system logs, network traffic, and application activity.
- Automated analysis: Advanced tools sift through the collected data, identifying patterns, anomalies, and potential security threats.
- Automated reporting: Insights gained from the analysis are presented in reports and dashboards, giving IT staff and management a clear picture of the organization's security posture.
- Automated response: Upon detecting an issue, the system can quickly alert IT administrators or take precautionary measures, such as blocking suspicious activity or isolating infected systems.
This approach allows for more efficient allocation of resources to address critical security issues promptly, making it highly effective against time-sensitive threats in the ever-changing landscape of cyber security.
Part 6: Popular Cyber Security Monitoring Tools
Choosing the right cyber security monitoring tool is critical for safeguarding sensitive data and ensuring business continuity. Below are three popular cyber security monitoring tools, each with its own set of features:
1. FamiGuard Monisen
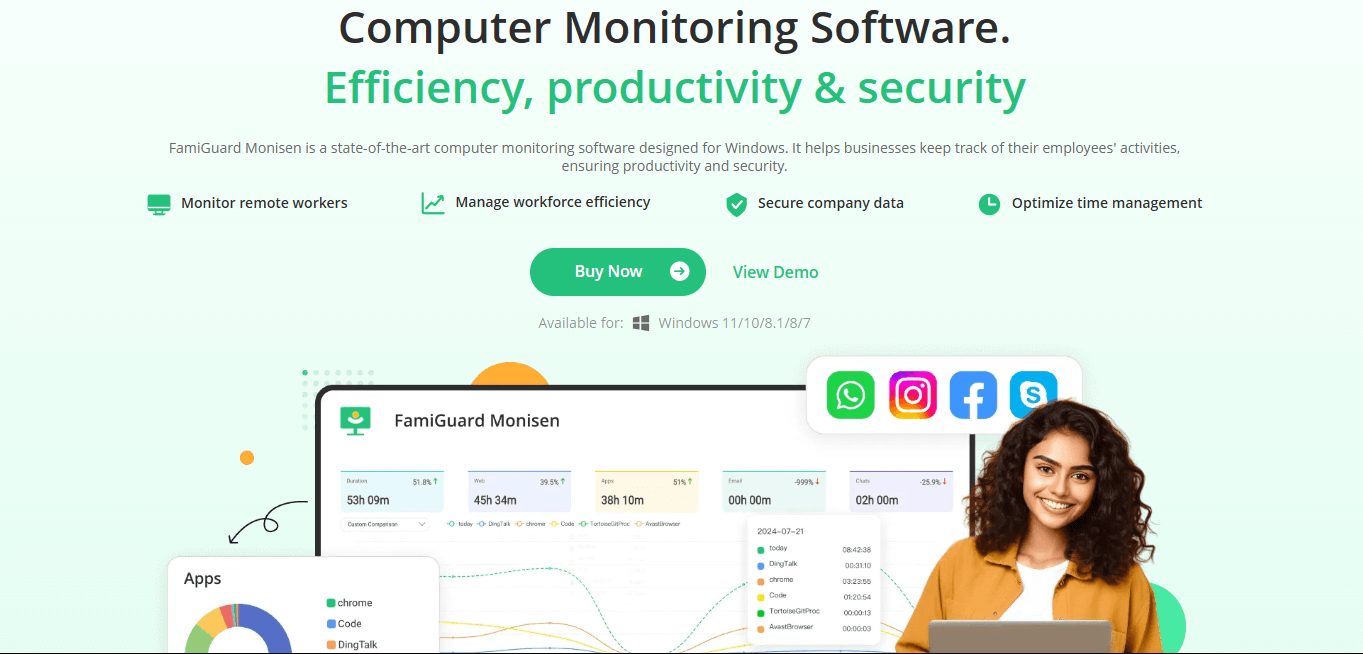
FamiGuard Monisen is a powerful monitoring tool designed specifically for businesses seeking effective employee monitoring. With advanced features for tracking user activity, logging keystrokes, monitoring web traffic, and capturing screen snapshots, Monisen provides comprehensive oversight for companies. It's ideal for improving employee productivity while ensuring the security of sensitive company data. FamiGuard Monisen excels in within a period of time monitoring, allowing administrators to respond quickly to potential security risks or breaches within the corporate environment.
- Comprehensive employee monitoring, including website activity, keystrokes, and app usage.
- Real-time alerts on suspicious behavior or potential insider threats.
- Detailed reports on user activity, including access to sensitive data.
2. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a robust solution tailored for IT professionals to detect, respond to, and prevent cybersecurity threats. This software offers within a period of time threat detection through automated event correlation, log management, and detailed reporting, making it a preferred choice for enterprises of all sizes. Its user-friendly interface simplifies the process of monitoring vast amounts of security data, while its integration with other SolarWinds tools enhances overall network security. SolarWinds is ideal for organizations that need continuous, proactive threat monitoring with minimal manual intervention.
- Real-time threat detection with customizable alerts.
- Automated responses to detected incidents.
- Centralized log management for easy auditing and reporting.
3. Splunk
Splunk is a leading cyber security tool known for its powerful data analytics capabilities. It specializes in monitoring and analyzing massive datasets to detect anomalies, security threats, and potential vulnerabilities in within a period of time. Splunk’s versatility lies in its ability to collect and interpret data from various sources across an enterprise, providing insights into security events, network performance, and user activity. This makes Splunk a top choice for large-scale organizations that require comprehensive security visibility, advanced threat detection, and detailed auditing tools for compliance purposes.
- Advanced machine learning capabilities for predictive analytics and anomaly detection.
- Scalable and flexible architecture that supports both cloud and on-premises deployments.
- Real-time event monitoring and forensic analysis tools.
Part 7: Challenges in Cyber Security Monitoring
As the complexity of cyber threats grows, organizations face several significant challenges in monitoring and defending their systems effectively. These challenges include managing vast amounts of data, dealing with false positives, and addressing the shortage of skilled cybersecurity professionals.
Data Overload:
With the increasing number of security tools and expanding attack surfaces, organizations need help managing the overwhelming volume of data generated. The nearly tripled network traffic since 2018 adds to the complexity, making it harder for security teams to focus on critical issues, leading to potential oversights in detecting real threats.
False Positives:
According to Security magazine, false positives are a significant issue in cyber security monitoring, with up to 20% of all cybersecurity alerts being false alarms. These alerts can lead to alert fatigue, causing security personnel to overlook real threats and save valuable time on non-issues, decreasing overall operational efficiency.
Skill Gap in Cybersecurity Workforce:
The cybersecurity field faces a significant workforce shortage, with 663,434 job openings in the US and only 1.1 million professionals available. This gap leaves organizations operating with just two-thirds of the required talent, making it harder to manage security monitoring effectively. The result is increased workloads for existing staff, leading to burnout and reduced performance.
FAQs about Cyber Security Monitoring
1. What is an example of security monitoring?
An example of security monitoring is using a Security Information and Event Management (SIEM) system to track and analyze within a period of time data from network devices, servers, and applications. This helps identify potential threats, such as unauthorized access or abnormal behavior, and allows for quick response to security incidents.
2. What are the 5 types of cyber security?
- Network Security – Protecting internal networks from attacks.
- Information Security – Securing data from unauthorized access or alterations.
- Endpoint Security – Safeguarding devices like computers and mobile phones.
- Application Security – Ensuring that software is secure from threats.
- Cloud Security – Protecting data and services in cloud environments.
3. What are the 7 pillars of cybersecurity?
The 7 pillars of cybersecurity are:
- Access Control – Managing who can access data and systems.
- Security Operations – Monitoring and responding to security incidents.
- Compliance and Governance – Ensuring legal and regulatory adherence.
- Risk Management – Identifying and mitigating security risks.
- Network Security – Securing network infrastructures.
- Incident Response – Preparing for and responding to cyberattacks.
- User Education and Training – Educating users on cybersecurity best practices.
4. What are the 7 layers of cyber security?
The seven layers of cybersecurity include:
- Physical Security – Protecting physical hardware and locations.
- Network Security – Securing internal and external networks.
- Perimeter Security – Defending the network perimeter with firewalls and intrusion detection.
- Endpoint Security – Protecting individual devices like laptops and mobile phones.
- Application Security – Securing software applications from threats.
- Data Security – Safeguarding sensitive information with encryption and access control.
- User Education – Training users to identify and avoid security threats.
Conclusion
Cyber security monitoring has proven to be a game-changer in safeguarding digital assets in today's interconnected world. Its importance is evident in its ability to detect threats, ensure compliance, and maintain business continuity. The tools and techniques discussed, from SIEM systems to continuous monitoring, provide organizations with the means to stay ahead of evolving cyber threats and protect their valuable data.
Cyber security monitoring is set to evolve further, driven by advancements in AI and machine learning. Despite challenges like data overload and the skills gap, the future looks promising for those willing to invest in robust monitoring strategies. By embracing these technologies and addressing current hurdles, organizations can build stronger defenses and create a more secure digital landscape.
By Tata Davis
An excellent content writer who is professional in software and app technology and skilled in blogging on internet for more than 5 years.