Protecting your child from online predators is essential in this complex Internet environment. With 72% of children worldwide encountering online threats such as cyberbullying and scams, safeguarding children has never been more critical. The rapidly developing Internet and teen social environment have only increased the time your child spends online, making parental controls a crucial tool in your arsenal to keep your child safe from online predators.
This article will guide you through identifying online predators, recognizing red flags, and using parental controls effectively. By understanding these key areas, you'll better protect your child in the digital world.

Table of Contents
Part 1: What Is an Online Predator?
Part 2: Red Flags of Online Predators
Part 3: How to Protect Kids from Online Predators?
Part 4: How to Do If There Is a Problem
Part 1: What Is an Online Predator?
Online predators are individuals who use the Internet to exploit and manipulate children and adolescents. Their primary goal is to build trust and connection with their victims, which can lead to a range of abusive behaviors, including solicitation of photos, threats, and even physical contact or abduction. Astonishingly, approximately half a million predators are active daily, grooming and soliciting children online.
1. Understanding the Threat
- Prevalence: Globally, 11.5% of children report unwanted online sexual solicitation. (Source: ScienceDirect)
- Risks: These predators lure children into sexual conversations, send obscene material, or request explicit pictures.
- Teen Vulnerability: Adolescents are particularly at risk as they might engage with predators out of curiosity or emotional attachment.
2. Methods of Operation
- Platforms Used: Predators frequent forums, social media, anonymous chat rooms, and other digital spaces popular with younger audiences.
- Anonymity Tactics: They often hide their identities, using fake profiles or pretending to be someone else to avoid detection.
- Grooming Process: This involves forming an emotional bond with the child to lower their inhibitions, often preparing them for abuse either online or offline.
3. Common Strategies and Crimes
- Engagement: Engaging in sexually explicit communication, sextortion, and arranging meetings for sexual purposes.
- CSAM (child sexual abuse material): Involvement in the collection, distribution, and production of child sexual abuse material, with over 29 million suspected exploitations reported in 2021.
- Social Media Deception: Predators may use fake profile pictures and share interests with their targets, often complimenting or offering gifts to build trust.
4. Traits and Behaviors
- Multiple Victims: Predators typically communicate with several victims simultaneously.
- Communication Channels: A significant percentage of sexual advances occur through internet chatrooms and instant messaging.
- Age Focus: Over 50% of online sexual exploitation victims are between the ages of 12 and 15.
By understanding these aspects, you can better safeguard your children from the dangers posed by online predators.
Part 2: Red Flags of Online Predators
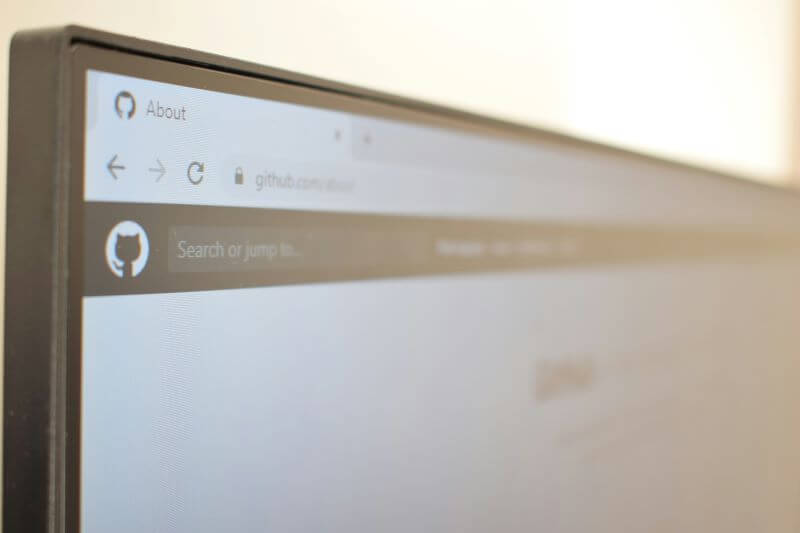
Online predators exhibit specific behaviors that can be warning signs for parents and guardians. Recognizing these red flags is vital to protect your child from potential harm. Here are the key indicators:
1. Excessive Attention and Flattery
Immediate Compliments: Predators often begin interacting with excessive compliments to gain a child's trust quickly.
Persistent Communication: They engage in frequent messaging to create a sense of intimacy and dependency.
2. Requests for Personal Information
Invasive Questions: Asking for details about personal and family life can be a strategy to isolate the child from trusted adults.
Solicitation of Photos: Requests for pictures, incredibly personal or compromising ones, are a common tactic.
3. Gifting and Promises
Offering Gifts: Items like gift cards, money, or expensive gadgets are used to lure and obligate the child.
Promises of Better Opportunities: Proposals such as modeling jobs or sponsorships can entice younger audiences.
4. Isolation Techniques
Driving a Wedge: Tactics such as pitting the child against their parents or suggesting that they cannot be trusted.
Exclusive Relationship: Efforts to make the child feel they have a unique, special connection that should be kept secret.
5. Threats and Manipulation
Intimidation: Threats to expose secrets or harm the child's family if they resist or decide to cut communications.
Sexual Advances: Initiating inappropriate conversations or pressuring for explicit material.
6. Warning Signs in Child Behavior
Secretive Online Activities: If your child is hiding screens or becomes anxious when unable to access the Internet.
Unexplained Gifts: Receiving items from unknown sources can indicate contact with a predator.
Withdrawal from Regular Life: Significant changes in behavior, such as withdrawing from family and friends, can be a red flag.
Understanding these signs is your first step in intervening and protecting your child from the dangers of online predators. Stay vigilant and maintain open communication with your child about their online interactions.
Part 3: How to Protect Kids from Online Predators?

1. Establish Open Communication
Encourage Honesty: Foster an environment where your child feels comfortable discussing online experiences without fear of judgment or punishment.
Discuss Online Risks: Regularly discuss online predators' dangers, emphasizing the importance of not sharing personal information.
2. Implement Parental Controls and Supervision
Use Technology: Install parental control software to monitor and restrict your child's online activities. Parents consider use FamiGuard Pro, the comprehensive parental control app to track the device phone.
With FamiGuard Pro, you can view received and sent messages, your kid’s call history, monitor popular social media like Facebook, set keywords alerts, track GPS locations and set geofence.
FamiGuard Pro is a nice assistant for you to guarantee your child’s online safety, combining parental control tool with proper education, it can decrease the risk of harassing from online predators.
How to Set Up FamiGuard Pro to Have Parental Control?
Step 1. Create/Sign in your account and pick the suitable subscription plan to unlock all FamiGuard Pro features.
Step 2. After purchasing, you will be navigated to Member Center. Click Start Monitoring button and you will go to the dashboard, choose the device you want to bind and follow the Set up guide to finish installation and configuration.
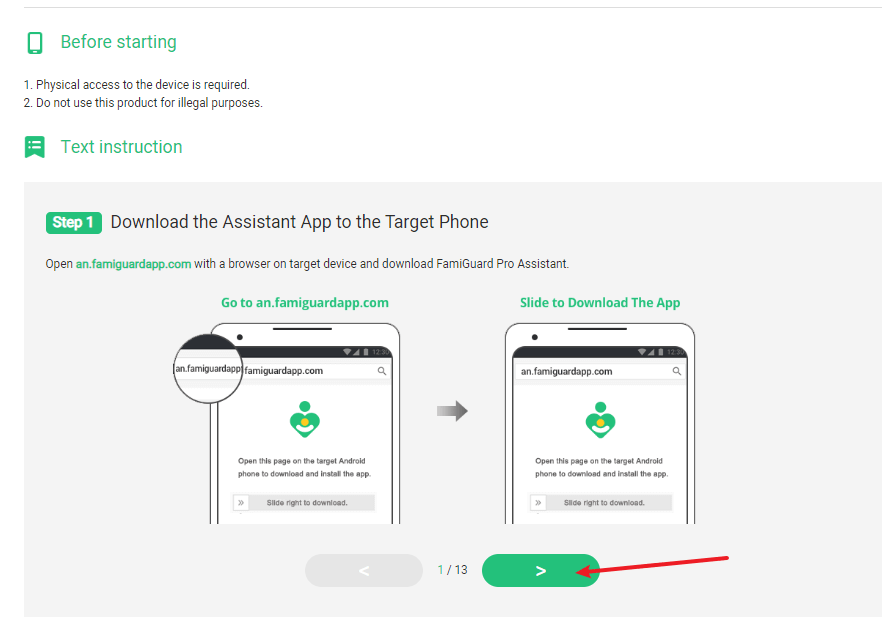
Step 3. If you verify your setup successfully, you can begin your monitor now. You can check call history, messages, monitor social apps and more. FamiGuard Pro has all features that a parental control tool needs to safeguard your child.
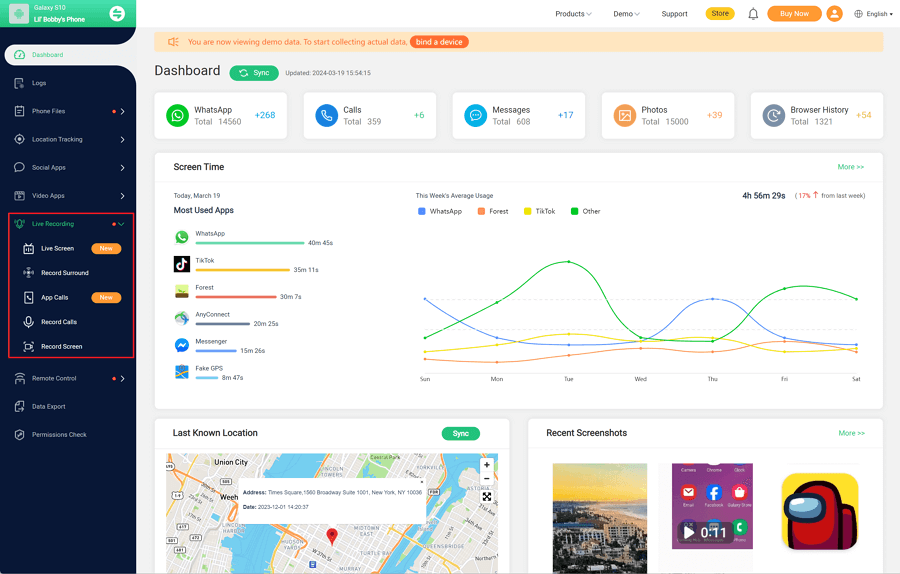

3. Educate on Recognizing Red Flags
Identify Suspicious Behavior: Teach your child to recognize grooming tactics like excessive compliments or gifts.
Know When to Exit: Explain how to safely disconnect from uncomfortable online interactions and report them to a trusted adult.
4. Promote Safe Online Practices
Set Privacy Settings: Ensure your child's private profiles and teach them to manage friend requests responsibly.
Be Cautious with Personal Info: Instruct your child never to share personal details like their location, school, or phone number online.
5. Utilize Educational Resources
Access Online Safety Tools: Direct your child to resources like NetSmartz.org to learn about internet safety.
Learn from Others: Engage with community forums or local workshops that focus on safeguarding children from online threats.
By incorporating these strategies, you empower your child with the knowledge and tools to navigate the digital world safely.
Part 4: How to Do If There Is a Problem
- Block and Report: Immediately block the predator on all platforms and report their profile to the service provider.
- Contact Authorities: Report the incident to local law enforcement or specialized agencies like the Child Exploitation and Online Protection Centre (CEOP).
- Emergency Situations: If a child is in immediate danger, call 911 or your local emergency number.
- Gather Evidence: Document all interactions, including messages, emails, and any other communications.
- CyberTipline Reports: Report any suspected online enticement or sexual exploitation to the CyberTipline at www.cybertipline.com.
- Counseling Services: Seek professional counseling for your child to help them cope with any psychological impacts.
- Support Hotlines: Utilize hotlines such as the National Sexual Assault Hotline (800.656.HOPE) or the National Child Abuse Hotline at 800.4.A.CHILD for immediate support.
- Understanding the Law: Be aware that adults involved in corrupting minors or engaging in sexually explicit conversations can be prosecuted under federal or state law.
- Sex Offender Registration: Convicted individuals are generally required to register as sex offenders.
These steps will ensure a structured response to protect your child from online predators and handle incidents effectively.
FAQs about Protecting Child from Online Predators
Q1: How can parents prevent online predators from targeting their children?
Parents and caregivers can take several steps to prevent child sexual abuse material and protect their children from online predators:
- Have conversations with your child about the risks of online predators.
- Maintain open communication channels with your child.
- Ensure your child's social media profiles are set to private settings.
- Monitor your child's online interactions and friendships.
- Utilize parental controls to restrict access to inappropriate content.
Q2: What strategies can I use to safeguard my child from predators?
To protect your child from predators, consider the following strategies:
- Encourage your child to speak up about anything that makes them uncomfortable.
- Educate your child about personal boundaries and the importance of respecting them.
- Teach your child appropriate ways to talk about their bodies.
- Always be available for your child to talk to and ensure they know they can come to you without fear of getting in trouble.
- Provide opportunities for your child to discuss new topics or concerns.
Q3: What actions can parents take to ensure their child's online safety?
Parents can use various technological tools and practices to keep their children safe online:
- Teach your child the importance of keeping personal information private.
- Check that privacy settings are secure to prevent strangers from accessing your child's information.
- Cover webcams when they are not in use to prevent unauthorized viewing.
- Use parental controls and safe search tools for younger children to maintain a positive online experience.
Q4: What are three essential safety tips for kids using the Internet?
Kids can follow these three important safety tips to stay secure online:
- Never share personal information, such as home address, phone number, or details about their school.
- Please choose a screen name that doesn't reveal real names and keep passwords confidential, sharing them only with parents.
- Only meet in person with people they have met online if they have parental permission and supervision.
Conclusion
The strategies for safeguarding our children against online predators outlined in this article, from recognizing the subtle tactics of predators to implementing robust parental controls, aim to empower parents with the knowledge and tools needed to protect their children effectively. Famiguard Pro emerges as a highly recommended tool, offering an additional layer of security in protecting kids' online safety. Its features support the vigilant monitoring and management of online interactions, making it an invaluable asset to shield our children from potential online threats.
Let this guide serve as a starting point for continued dialogue and action within families and communities, striving towards a world where children can explore the vast Internet resources without fear.

An Array of Amazing Features
-
Track cell phone location in real time and view location history
-
Check all incoming and outgoing calls & SMS
-
Spy on social media apps like WhatsApp, Instagram, Snapchat, Facebook, Viber, WeChat and more
-
Remotely access the files on the target phone, like contacts, photos, call logs, etc.

By Tata Davis
professional in software and app technology, skilled in blogging on internet
Thank you for your feedback!