Phone tracking affects more than 50,000 people annually. The scariest part? Most victims discover the privacy breach when it's already too late.
Your smartphone contains your entire digital life. Personal messages, banking information, location data, and private photos - everything lives there. Knowing whether someone tracks your phone isn't just about privacy. It's about staying safe from stalkers, cybercriminals, and anyone who wants to monitor your activities without your permission.
Here's the good news - we have solutions. This complete guide reveals 10 warning signs to know if someone is tracking your phone. You'll learn exactly what steps to take next. Let's keep your personal information safe.
Table of Contents
Part 1: Understand Phone Tracking Methods
The ability to protect your privacy depends on knowing how others can track your phone in today's digital world. Your smartphone leaves different digital footprints that others can monitor through several sophisticated methods.
Common Types of Phone Tracking
Your phone can be tracked through three main methods:
| Tracking Method | How It Works | Level of Accuracy |
|---|---|---|
| GPS Tracking | Uses satellite signals | Highest (within meters) |
| Cell Tower Triangulation | Measures signal strength between towers | Moderate (300m radius) |
| Wi-Fi Positioning | Tracks through nearby networks | High in urban areas |
Legal vs. Illegal Tracking
Phone tracking isn't always malicious. Legal tracking has sections that cover:
- Parental monitoring of children's devices like using FamiGuard Pro
- Employee monitoring on company-provided phones
- Emergency services location tracking
- Find My Phone services for lost devices
Illegal tracking happens when someone monitors your phone without consent. This can lead to serious legal consequences. Violators face fines and imprisonment under federal laws like the Electronic Communications Privacy Act.
Who Might Track Your Phone and Why
Several entities track phones for different reasons:
- Law enforcement (with proper warrants)
- Emergency services for 911 calls
- Parents monitoring minor children
- Employers monitoring company devices
Legitimate Trackers
- Cybercriminals seeking personal information
- Stalkers monitoring location
- Data brokers collecting behavioral data
- Malicious apps gathering personal information
Potential Threats
Your phone's location data is particularly valuable for marketers and advertisers. That's why these apps often ask for location permissions and collect more data than they need for their stated functions. Some tracking benefits services like navigation or emergency response, but unauthorized tracking risks your privacy and security.
Your phone can still be tracked through cell tower triangulation or Wi-Fi networks, even with location services turned off. This knowledge helps you make better decisions about your device's security settings and app permissions.
Part 2: What Are Physical Signs of Phone Tracking
Your phone shows subtle signs when someone tracks it, and spotting these early warning signals helps detect unwanted surveillance. A monitored smartphone displays specific physical symptoms, and identifying these signs is vital to protect your privacy.
Battery Performance Issues

Unusual battery behavior is one of the clearest indicators of phone tracking. Tracking software runs constantly in the background and drains more power than usual. Look for these warning signs:
| Battery Warning Sign | What It Means |
|---|---|
| Battery drains quickly while idle | Background tracking activity |
| Battery life varies unexpectedly | Sporadic monitoring sessions |
| Power depletes faster than before | Continuous data transmission |
You can check if your battery drain seems suspicious by comparing it with another phone of the same model. If your device uses a lot more power in similar conditions, someone might have compromised it.
Unusual Device Temperature
Your phone's temperature patterns can reveal hidden tracking activities. Phones naturally warm up during heavy use, but specific temperature changes should concern you:
- The device feels warm without active use.
- Heat builds up at the back consistently.
- Temperature rises in standby mode.
Watch out if your phone feels warm without running apps or charging. This might indicate secret background processes that monitor your activities.
Strange Sounds and Interference
Clear connections are standard in modern digital networks, so odd sounds during calls might point to surveillance. Be alert to:
- Clicking or popping noises during calls.
- Static or electronic interference.
- Echo or distant voices in the background.
- Disruption with nearby electronic devices.
A tracked phone often disrupts other electronic devices nearby. Try placing your phone next to a radio or TV - unusual static or interference when the phone sits idle might indicate unauthorized monitoring.
A single sign may not prove tracking, but multiple symptoms occurring together need immediate attention. These physical signs should prompt you to take steps to protect your privacy and security.
Part 3: Recognize Digital Warning Signs of Secret Monitoring
Modern smartphones leave digital footprints that reveal if someone monitors your phone activities. These electronic breadcrumbs prove more reliable than physical signs to detect tracking.
Suspicious Data Usage Patterns
Data consumption patterns on your phone can indicate tracking software. Look out for these signs:
| Normal Data Usage | Suspicious Patterns |
|---|---|
| Matches app usage | 5x higher than app reports |
| Consistent patterns | Unexplained spikes |
| Stops when apps close | Continues during idle time |
Your device might have hidden tracking software if total data usage is substantially higher than individual app usage combined.
Unexpected App Behavior
Apps can show signs of unauthorized tracking through unusual patterns:
- Apps asking for permissions unrelated to their function (like a calculator wanting camera access)
- Stable apps that suddenly crash or slow down
- Unknown apps appearing on your device
- Standard apps that need extra permissions after updates
Watch apps that ask for location, camera, or microphone access without needing these features. A simple reminder app doesn't need your camera or location.
Strange Text Messages or Notifications
Tracking attempts often show up through suspicious messages. Watch out for:
1Text messages with unknown links, especially those claiming to be from trusted services like USPS.
2Messages about urgent delivery issues or account problems.
3Notifications asking for personal information or login credentials.
4SMS messages that contain spelling or grammar mistakes.
Important Warning: Links in unexpected text messages should never be clicked, even from seemingly legitimate sources. USPS and other legitimate services won't send tracking information with clickable links.
Your phone's behavior patterns need close monitoring, especially after new app installations or system updates. Someone might have compromised your device's security if you notice unexpected changes in data usage, app behavior, or message patterns. Tracking software stays hidden but can't mask all its digital traces.
Part 4: Learn about Surrounding People's Behavioral Red Flags
Your phone might be tracked even without technical signs showing up. People's behavior around you often gives away the first hints that someone has compromised your privacy.
People Knowing Your Location Without Asking
Someone knowing where you are without asking should raise red flags. These patterns might reveal unauthorized tracking:
| Normal Behavior | Suspicious Behavior |
|---|---|
| Asking about your plans | Already knowing your exact location |
| General location awareness | Specific detail about your movements |
| Coincidental meetings | Frequent "unexpected" encounters |
Pay special attention to people who show up repeatedly at your locations without any prior discussion about your plans. This behavior suggests they might access your location data secretly.
Unexplained Account Activities
Your digital footprint can expose unauthorized tracking through several account activities:
- Login attempts from unknown devices or locations
- Account settings changes you didn't authorize
- Video call minutes increasing without making calls
- Unfamiliar searches in your history
- Unknown apps appearing on your device
Your device might be monitored if Google activity shows searches you never made or your device name looks different (like "Samsung SM-G998U" instead of "Galaxy S21 Ultra 5G").
Suspicious Social Media Interactions
Unusual patterns on social media platforms often reveal tracking attempts. Watch out for:
- Comments about your activities before you post them
- Messages mentioning places you've visited but haven't shared
- Friend requests from strangers who know your routine
- Tags in locations you've been to without sharing
- Comments revealing details from your private conversations
Important Warning: Check your connected devices and active sessions right away if you spot unfamiliar activity on your social media accounts. Someone might have unauthorized access.
Multiple red flags need immediate attention, though a single incident might be coincidental. Trust your gut - if others' interactions with your digital presence feel strange, check your device's security immediately.
Part 5: How to Find Out Unwanted Phone Tracking
After spotting suspicious signs, you should check your device thoroughly. Your smartphone has powerful tools that help you verify if someone tracks your activities.
Using Built-in Security Features
Your smartphone's native security features protect you first. Here's how you can access them:
1For iPhone:
Step 1: Go to Settings > Privacy & Security > Location Services
Step 2: Check "System Services" for significant locations
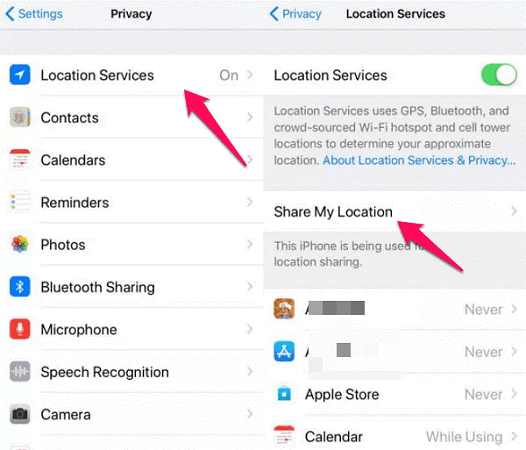
Step 3: Review "Share My Location" settings
Step 4: Get into which apps have location access
2For Android:
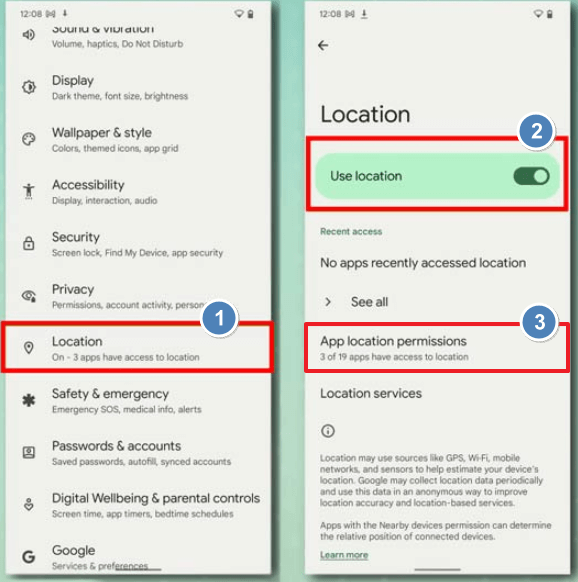
Step 1: Go to Settings > Security & Privacy
Step 2: Check "Permission Manager" for suspicious apps
Step 3: Review "Location History" in Google settings

Step 4: Look for unknown entries in "Device admin apps"
Running Security Scans
Your device gives you multiple ways to scan for tracking software:
| Scan Type | What It Checks | When to Use |
|---|---|---|
| System Scan | Core security threats | Weekly |
| Permission Scan | App access rights | Monthly |
| Security Audit | Overall device health | Quarterly |
Checking App Permissions
App permissions show potential tracking. Here's what you need to watch:
High-Risk Permissions to Review:
- Location access (especially "always allow")
- Microphone usage
- Camera access
- Contact list
- Storage permissions
Your app permissions need proper management:
Step 1: Go to Settings > Apps > Permissions.
Step 2: Review each permission category and look for apps with too much access.
Critical Warning: Watch out for apps that:
- Ask for more permissions than needed
- Keep running in the background
- Use generic or system-like names
- Were installed when you first noticed tracking signs
Check your device's admin settings regularly. Some tracking apps hide as system utilities and need admin access to work. Remove admin rights from apps you don't trust.
Make sure your apps come from official stores. Good apps clearly state what permissions they need and why. An app that asks for permissions it shouldn't need raises a red flag. You should act quickly.
The context matters when you look at permissions. Navigation apps need location access. Calculator apps don't. Trust what you feel – if an app's permissions seem wrong, dig deeper or remove it.
Part 6: How to Stop Unwanted Phone Tracking
You need a smart plan to stop unwanted phone tracking. This includes quick actions and long-term security steps. Here's a detailed guide to help you take back control of your device, whether you know or just think someone's tracking you.
Immediate Security Measures
Time matters when you find tracking software on your phone. Here are the steps you should take right away to protect your privacy:
| Security Action | iPhone Steps | Android Steps |
|---|---|---|
| Factory Reset | Settings > General > Reset | Settings > System > Reset |
| Update OS | Settings > General > Software Update | Settings > System > System Update |
| Remove Apps | Press and hold > Delete App | Settings > Apps > Uninstall |
Before You Start: Back up your essential data, like contacts and photos, before a factory reset. Be careful about what you restore to avoid bringing back any tracking software.
Long-term Protection Strategies
You need a detailed security approach to protect your phone from future tracking. Here's your protection plan:
- Install a reliable VPN service
- Enable two-factor authentication on all accounts
- Keep security software updated
- Manage app permissions carefully
- Watch your network security
FAQs about Phone Tracking
1How can you tell if your phone is under surveillance?
To determine if your phone is being tracked, look for unfamiliar apps you didn't install, monitor your app usage for unrecognized activity, and observe any unusual spikes in data usage. Additionally, an anti-spyware tool can help identify any tracking signs on your device.
2What steps can I take to identify a tracker on my phone?
To detect a tracker on your phone, navigate to Settings, tap Safety & Emergency, and select Unknown tracker alerts. From there, you can initiate a manual scan, which takes about 10 seconds to complete and helps you identify any trackers nearby.
3Is it possible for someone to track my mobile phone without my knowledge?
Yes, your phone can be tracked without your awareness if it is infected with malware or spyware. This can lead to unauthorized tracking of your location, even if location services are disabled, and may also result in the theft of personal information or a slowdown in your device's performance.
4What is the unique code to check if my phone is tapped?
For phones on CDMA networks like Verizon or US Cellular, dialing *72 can reveal if calls or data are being redirected. Dialing *#002# on GSM networks can help you discover if your phone is tapped by showing any call forwarding settings.
Conclusion
This post shows you the signs if someone is tracking your phone. Physical signs like battery drain, digital clues like suspicious data usage, and behavioral red flags will help you protect your digital privacy.
It is the right thing to actively protect your device's security. Watch your phone's behavior patterns, update your software regularly, and act on warning signs of potential issues. Your instincts matter - unusual patterns or behaviors should prompt you to secure your device and protect your privacy immediately.
What's more, if you want to keep your kids' phone safe with setting parental control on it and know it's app library, you can use FamiGuard Pro. This is a safe and legal parental control app to solve your concern.
By Tata Davis
An excellent content writer who is professional in software and app technology and skilled in blogging on internet for more than 5 years.
Thank you for your feedback!