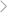So, are you wondering how to remove a hacker from my phone?
Hacking happens everywhere. No matter what kind of device you have, there's always a risk of it getting hacked. You see, hacking can happen to anybody. Whether they're kids or adults, as long as there's a chance and opportunities, hackers will always strike unexpectedly.
If you feel like your phone is getting hacked, then there's nothing much to do but treat it immediately. In this article, we'll explain some tips to make your phone safe and get further away from hackers.
Table of Contents
Part 1: What can Hackers Do on Your Phone?
Before knowing how to remove a hacker from my iPhone, better if we understand their perspective first. Why do hackers hack anybody’s phone in the first place?
There are various reasons for this like obtaining the user’s personal data to be sold in the black market, stealing sensitive data to gain access to users’ personal accounts, and many others. Hackers not only attack the government but also the people in general. As we’ve previously stated, as long as there’s a chance to do it, hackers will engage in hacking.
Hackers want to hack your phone for various purposes, such as:
1. Check and Collect Your Phone Files
Before learning how to remove a hacker from my phone number, we want to explain to you this one point. What hackers would do the first time they got into your phone is to obtain the files and personal data. And talking about the files, they can snatch any files stored in your phone, even the ones you set as hidden.
When they got these files, there's a chance that they will leak them to the internet, definitely ruining your privacy, security, and also reputation. Surely, information leaking like this is truly dangerous, especially for companies and government agencies. That’s why these big companies usually set more complex security measures to make sure that the hacking risks are put at a minimal level.
2. Track Your real-time Location
While they get access to your phone, they will also try to track your location as well. The reason? To find your actual address, of course. When they know your actual locations, they can work with their tools to hack not only your phone but also the other peripherals in your home. Therefore, it’s easy for them to attack you from a psychological aspect.
When your actual location is known, the one who's at risk is not only you but also the other family members. That’s the main reason why leaking your number and address to the internet is definitely a bad idea.
3. Record Your Passwords
When the hackers get into your phone, they will likely put the keylogger apps as well. These apps work by recording any typing done on the phone and even especially focus on the times when you put in the credentials to log into your accounts.
The recorded typings will be sent directly to the hackers, gaining access to all of your accounts, which is pretty bad. Therefore, when you see and feel that your phone starts acting up, it's probably a good idea to reset and do the clean installation again. Resetting your phone will result in data loss, so better to back up your data before doing it.
4. Control Your Camera
They can access all parts of your phone, including the microphone and the camera. When they get access to your camera, they can basically look into you directly from the camera. You can’t notice whether the camera is recording or not, because it's operated no through the default way, but via hacking tools.
The hackers will basically be able to see all of your activities, including the private ones as long as the camera is facing you. Some people decided to put tape on their cameras, but that’s not actually a good idea to protect yourself. Instead, putting on some good antivirus may work better in fighting the hacking attempts.
Part 2: 6 Signs of a Hacked Phone
There are a few signs that your phone got hacked, such as:
1. Shortened battery life

So, how to remove a hacker from my phone code? Well, there are a few to get the job done. But first, let’s learn about the signs.
The first and probably the most noticeable is the battery drain. When your phone got hacked, the battery tends to drain way more quickly than usual.
2. High mobile data usage

When you don’t even use the phone that often, you can still see the amount of data usage. This is because the tools installed will always try to connect to the internet. So if you see unusually high data usage on your phone, it’s probably a clear sign.
3. Unfamiliar Apps

So, how to remove a hacker from my Samsung phone? By removing the unusual apps, of course.
If you start noticing some weird apps appearing, that can be an indicator that your phone got hacked.
4. Frequent Pop-ups
The pop-up ads are indeed very annoying, and it’s even more intrusive when your phone got hacked. The ads will show up more often, and the frequency is definitely higher than before.
5. Slower Speeds

Hacked phones can also experience slowing in performance. It’s real bad to the point to make the phone barely usable.
6. Unwanted Advertisements
If you start noticing some weird ads appearing on your phone, that might also be an indicator that your phone got hacked.
7. Unrecognized Texts and Emails.

People who got their phones hacked also reported that they received various texts and emails from unknown parties.
Part 3: How to Remove Hackers from My Phone
So, how to remove hackers from android and how to remove hackers from iPhone? You can actually do some tips below:
1. Remove Unfamiliar Apps
Removing unfamiliar apps from your iPhone can help protect your device from potential hacking attempts. It's important to regularly review the apps on your device and remove any that you don't recognize or trust. Additionally, be sure to only download apps from reputable sources, such as the Google Play Store or Apple App Store.
2. Review App Permissions
Removing app permissions can help to prevent hackers from accessing your Phone. Here's how you can remove app permissions on your Phone:
-
Go to "Settings" on your Phone
-
Scroll down and select the "Privacy" option
-
Tap on "Microphone" or "Camera" to review the apps that have access to these features
-
Turn off access for any suspicious or unfamiliar apps that you do not remember granting access to
-
Repeat the process for other permissions such as "Contacts", "Location", "Photos", and "Calendars
By regularly reviewing app permissions and being cautious about granting access to your device, you can help protect your Phone from hackers and prevent them from gaining unauthorized access to your sensitive information.
3. Update the operating system
One way to remove hackers from your iPhone is by updating the operating system. Hackers often exploit vulnerabilities in older versions of operating systems, so updating to the latest version can help protect your device.
Here's how you can update your iPhone's operating system:
-
Connect your iPhone to a Wi-Fi network.
-
Go to Settings > General > Software Update.
-
If an update is available, tap Download and Install.
It's important to note that before you update your operating system, you should back up your device to iCloud or your computer. This ensures that your data is safe in case something goes wrong during the update process.
Tips: How to Hack Someones Phone [Have a Try]
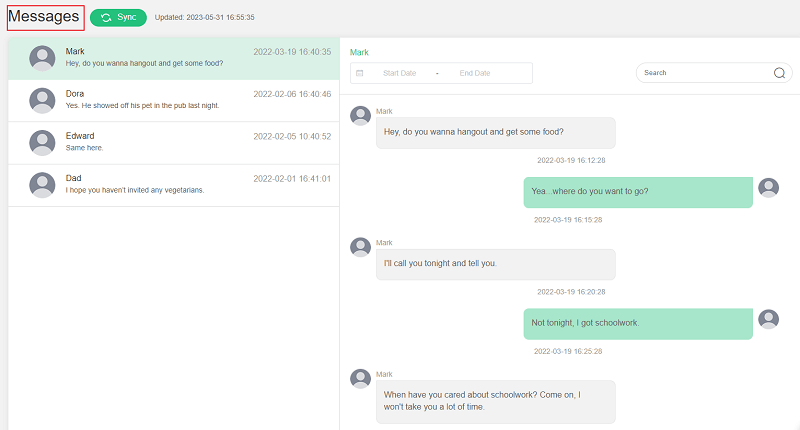
Has your phone been hacked? Has your privacy been snooped on? And are you upset because of it? Would you like to get into someone else's phone? Give it a try, now FamiGuard Pro can help you do just that, and the process is very simple and only requires you to have physical access to the target phone!
FamiGuard Pro
Rate:
Here is how to use it:
Step 1: Create your account for FamiGuard Pro for Android
Step 2: Download the Phone-hacking App from the given address
Step 3: Set it up on the target smartphone.
Step 4: Log into FamiGuard Pro for Android online dashboard, then you can monitor all kinds of activities on target phone

Amazing Features of FamiGuard Pro for Android
-
Monitoring Social Media Apps: Viewing messages or pictures on WhatsApp, Tiktok, Facebook, Instagram, Snapchat, Viber, WeChat, and more
-
Keylogger Feature: It has a keylogger feature that records everything typed on the keyboard.
-
Stealth Mode: No app icon appears on the target phone and the monitored person will not detect that you are spying on his phone
-
Remote Control: You can view his or her Instagram messages and pictures remotely, without touching the target phone.
By Tata Davis
An excellent content writer who is professional in software and app technology and skilled in blogging on internet for more than 5 years.
Thank you for your feedback!