Many people often opt for iPhone rather than Androids because of multiple reasons. One of them being more secure and not-hackable compared to Android phones. But is this really true? If not, then how to hack an iPhone?
Hacking into an iPhone is possible, but it might not as easy as it seems. There are specific hacking methods that you can use to hack this phone, but you have to be patient and mindful when learning about all of this new stuff.
In this article, we only want to share the basics of iPhone hacking, along with tips to prevent the same thing from happening to your phone.
Part 1: Can an iPhone Be Hacked?
Before getting to know how to hack. an iPhone, let us talk about this for a second.
In short, the answer is yes. All phones are basically hackable. And although the developers always try to update the security now and then, the hackers will always find the tiniest crack in the system that they could use as a gateway to enter it.
Hacking into a system that's already known for its security, like iPhone, won't be harder technically. That's the reason why most of these methods are usually related to human errors. People always make mistakes, and you could use the chance to turn their device into yours. So, rather than trying too hard to hack them through technical aspects, luring the people and making them enter their credentials without their knowledge would be a lot more effective.
Part 2: How to Hack an iPhone?
1. FamiGuard Pro - The Easiest Way to Hack an iPhone
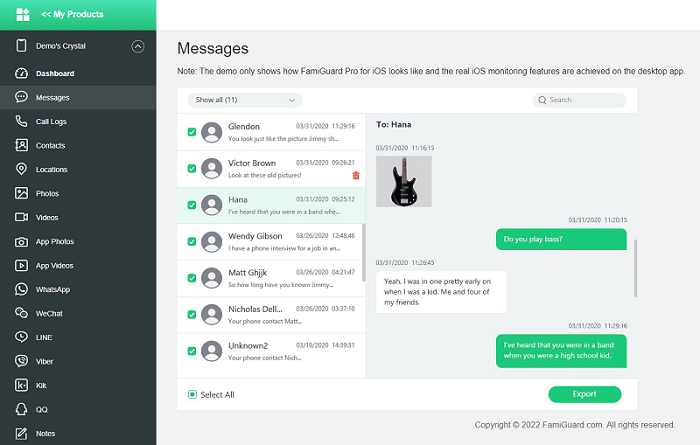
If you want to ask "how to hack someones iphone?", then FamiGuard Pro for iOS is your best choice. It will help you scan the iCloud data. In this way, you could easily get into someone's iPhone without password.
-
View iCloud Data:View someone's iCloud data without the target's iOS device.
-
Monitor Message: Monitor SMS, WhatsApp, LINE, Viber and Kik chat history, as well as exchanged media files, emojis and more
-
View Safari History & Bookmarks: Check Safari history and bookmarks to learn what the target user has been visited and what he is interested in.
To hack iPhone using FamiGuard Pro for iOS, follow these steps:
Step 1: Sign up for a FamiGuard Pro account with a valid email.
Step 2: Purchase a plan and download the app onto your computer, following the setup guide.
Step 3: Use the on-screen instructions to access the target's iPhone data.
2. Hack an iPhone with Wi-Fi Spoofing
Wi-Fi spoofing, also known as a man-in-the-middle attack, involves creating a fake Wi-Fi hotspot that appears to be a legitimate one in order to trick users into connecting to it. Once connected, the attacker can intercept and access the user's data, such as login credentials or other sensitive information.
Generally, to carry out a Wi-Fi spoofing attack, the attacker creates a Wi-Fi network with a name that is similar to a legitimate one, such as "Starbucks Wi-Fi" or "Free Public Wi-Fi." When a user connects to the fake network, the attacker can intercept the user's data and potentially gain access to their device and its data.

That's probably why many websites recommend that readers never use a wifi connection unless they're protected with a VPN. If you're wondering how to hack into iPhone successfully, creating a fake website will be at the top.
3. Hack into iPhone with Apple ID
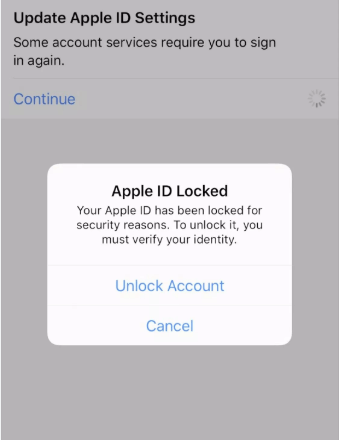
While it is not impossible for someone to hack your iPhone through your Apple ID, it is relatively difficult to do so. To gain access to an iPhone through an Apple ID, an attacker would need to obtain your Apple ID credentials, which typically include your email address and password. They may try to obtain this information through keylogger apps.
Once an attacker has access to your Apple ID, they may be able to access any associated devices, including your iPhone. They could potentially to monitor your actions, break into your iCloud account, view your visual media, and even track your precise location through "Find my iPhone", remotely lock or wipe your device, or access any data stored on it.
Part 3: Signs Your iPhone Is Hacked
And that's how to hack an iPhone remotely free. We know that it would be very stressful when the same thing happens to you. Therefore, we also want to tell you about the victim's perspectives. There are several signs you might notice when your phone is getting hacked.
Contacts or photos have been deleted
In case you observe any unauthorized deletion of contacts or photos from your iPhone, it may indicate that your device has been hacked. Certain malware can infiltrate your iPhone's data, including contacts and photos, and erase them without your consent. If you detect any missing or deleted data, it is vital to probe the reason and adopt measures to safeguard your personal information.
Strange pop-ups or notifications
Of the issue, these could be signs of malware or a virus on your iPhone, which can display deceptive messages to lure you into clicking on them. To avoid falling victim to such scams, refrain from clicking on any unexpected or suspicious pop-ups or notifications and investigate the underlying cause of the issue.
Fast Draining of Battery
If your iPhone's battery life is suddenly draining more quickly than usual, it could be a sign that there is malware running in the background and using up resources. Malware can cause your iPhone's CPU to work harder than usual, which can lead to a faster battery drain. If you notice that your iPhone's battery life is significantly shorter than usual, it's important to investigate the cause and take action to protect your device.
Part 4: How To Prevent an iPhone from being Hacked
So, that is how to hack someone iPhone remotely. If you have suffered from hacking attempts, there are a few things you can do to make yourself more protected in the future.
Update iPhone system regularly
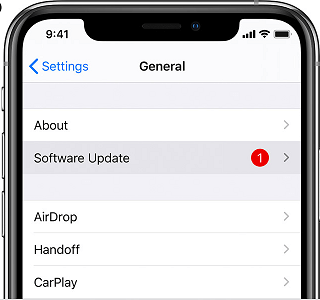
Keeping your iPhone updated with the latest app patches and updates is important in preventing hacking attempts. These updates often include security fixes and improvements that address known vulnerabilities in the software. To update your iPhone, go to Settings > General > Software Update. If a new update is available, follow the on-screen instructions to download and install the update.
Be cautious of suspicious messages or emails
Phishing scams and other types of social engineering attacks are common ways that attackers try to obtain sensitive information from iPhone users. To protect yourself from these attacks, be cautious of messages or emails from unknown senders and never click on links or download attachments from suspicious sources. If you receive a suspicious message or email, delete it immediately and do not respond to it.
Don't jailbreak your iPhone
Jailbreaking an iPhone involves removing software restrictions and limitations that are put in place by Apple. While this can give users more control over their devices, it also weakens the device's security measures and can make it more vulnerable to hacking attempts. To prevent jailbreaking your iPhone, do not attempt to modify the software or install apps from untrusted sources. Use only trusted apps from the official App Store and avoid apps that have a history of security or privacy issues.

By Tata Davis
professional in software and app technology, skilled in blogging on internet
Thank you for your feedback!